Agent Security Competitive Landscape Analysis
TL;DR
Agent Security refers to the controls needed to safeguard AI agents that access data and execute actions rather than just generate text. As deployment of AI agents accelerates, the market has begun to consolidate around five key capability areas: Identity & Access, Posture, Runtime Protection, Runtime Authorization, and Compliance. Most vendors concentrate on one or two of these, so understanding coverage patterns is essential when evaluating solutions for production environments, governance needs, and operational risk.
Agent Security has quickly become essential for organizations deploying AI agents that interact with tools, systems, and critical data. This competitive landscape analysis explains how the market is evolving, where common capability gaps appear, and how to frame vendor comparisons meaningfully.
What is Agent Security?
Traditional AI security focused on prompts and content filtering. But once a system can act, invoking tools, querying databases, creating records, or triggering workflows, the risk model changes.
Modern agents can call tools, access sensitive environments, and complete multi-step processes across SaaS apps, internal APIs, and Model Context Protocol (MCP) servers. In this context, security encompasses more than preventing unsafe outputs: it must address who the agent is, what resources it can reach, what behaviors it exhibits at runtime, and whether sensitive actions should require approval before execution. Provided these systems can operate autonomously and span multiple environments, governance and compliance evidence becomes equally important.
In practice, organizations are now thinking about Agent Security as a combination of five capability areas that show up in the competitive landscape: Identity & Access, Posture, Runtime Protection, Runtime Authorization, and Compliance.
The Agent Security Competitive Landscape
The competitive landscape is most meaningful when viewed through the lens of capability areas that reflect real operational needs. Each area represents a distinct set of risks and tooling approaches.
Identity & Access (Identify agents)
At its core, this layer determines whether an organization can reliably identify agents, assign appropriate identities, and control what systems they may interact with. Establishing identity and access boundaries is a prerequisite to responsible deployment, especially in environments with sensitive data.
Vendors such as Oasis Security, Token Security, Astrix Security, and Defakto Security emphasize identity governance, while enterprise players like CyberArk and Silverfort bring established controls into agent workflows. These solutions help establish foundational control before agents scale across teams and environments.
Posture (Observe behavior)
Once agents exist in an environment, visibility into their behavior and configurations becomes imperative. Posture reflects continuous monitoring, inventory, risk scoring, and governance over time. It provides an insight into who created agents, what resources they access, and how their activity evolves.
Solutions such as Zenity focus on comprehensive posture capabilities, while vendors like Geordie, Noma Security, Pillar Security, and NeuralTrust combine posture with adjacent controls. Even security incumbents such as CyberArk appear in this layer, demonstrating how traditional governance is extending into AI agent monitoring.
Runtime Protection (Secure execution)
Runtime Protection refers to controls applied while an agent is executing actions, including inspection of tool calls, enforcement of policies at the moment of invocation, and blocking unsafe execution paths. This capability becomes critical as agents graduate from testing to production roles with real operational impact.
In the landscape, NeuralTrust and Noma Security represent platforms emphasizing secure execution, alongside broader cybersecurity vendors like Cato Networks and Wallarm, which extend runtime protections into agentic workflows.
Runtime Authorization (Approve actions)
For high-risk operations, such as exporting sensitive data, modifying critical systems, or triggering irreversible actions, runtime authorization enables policy-driven gating or human approval. This introduces an additional layer of control beyond monitoring and enforcement.
Vendors positioned in this area, including NeuralTrust, Cato Networks, and Wallarm, emphasize the ability to require explicit approvals or policy checks before executing sensitive steps, helping organizations align security posture with operational policy.
Compliance (Monitor compliance)
Governance and regulatory requirements demand not only control but also evidence. Compliance tooling focuses on tracking adherence to policy, supporting reporting, and maintaining an audit trail across agent activity.
Companies like Credo AI and Holistic AI appear in this area, supported by platforms such as Pillar Security that bridge posture and compliance needs. These solutions help organizations demonstrate alignment with internal standards and external regulatory expectations.
Market Players Overview
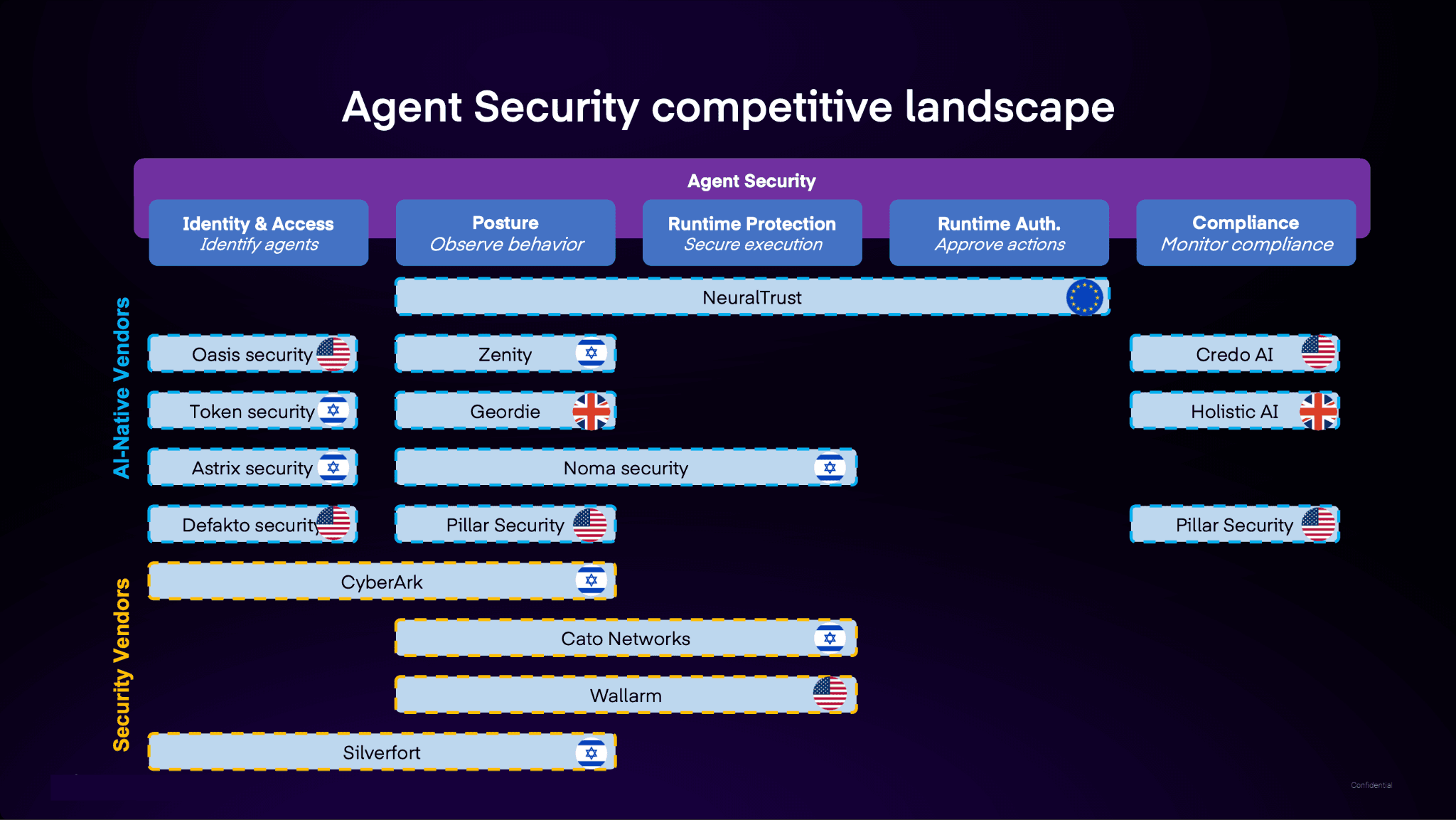
Across the agent security landscape, the differences between vendors are about strategic emphasis. Some companies have been built specifically for agentic systems. Their products are designed around dynamic execution, tool workflows, and autonomous behavior. Others come from broader enterprise security backgrounds, adapting familiar strengths like identity management, access control, and policy governance to the world of AI agents.
Because most platforms concentrate their capabilities around one or two problem areas, a simple brand comparison rarely tells the full story. Specialist providers tend to deliver deeper coverage where they focus, while incumbents often bring stronger integration within existing security and governance infrastructure. Looking at where vendors align within the landscape reveals a more practical picture of how well they meet each real agent security need.
Below are brief contextual profiles that capture how each vendor’s positioning relates to the agent security competitive landscape:
NeuralTrust
NeuralTrust is the only player that spans three central capability areas: Posture, Runtime Protection, and Runtime Authorization. Forms a cohesive loop of observing, securing and approving for agentic systems.
Zenity
Zenity is aligned with Posture-oriented capabilities, geared toward visibility, inventory, and governance of agent behavior.
Noma Security
With placement in both Posture and Runtime Protection, Noma emphasizes behavior observation paired with execution controls.
Pillar Security
Pillar bridges Posture and Compliance, reflecting strengths in monitoring and governance contexts as well as compliance reporting.
Oasis Security
Oasis appears in Identity & Access, specializing in agent identification and access governance.
Token Security
Token Security focuses on Identity & Access, particularly around permissions and access pathways.
Astrix Security
Astrix emphasizes identity and access management for agents as they connect to tools and data sources.
Defakto Security
Defakto is also positioned in Identity & Access, with an emphasis on access governance.
Credo AI
Credo AI is aligned with Compliance, reflecting a governance and standards perspective.
Holistic AI
Holistic AI operates in Compliance as well, focusing on governance and monitoring requirements.
CyberArk & Silverfort
These security incumbents contribute identity and posture-oriented governance at the foundational layer.
Cato Networks & Wallarm
Both appear across Runtime Protection and Runtime Authorization, indicating a combined emphasis on secure execution and controlled approvals.
What is the Best Option?
The best agent security solution depends on the company's priorities and needs. However, the landscape sheds light on the fact that most vendors do not cover all five capability areas equally.
For teams establishing foundational controls, Identity & Access and Posture are logical starting points. These layers help create a controlled environment where risk and permissions are visible. When agents are deployed in production with access to sensitive resources, Runtime Protection and Runtime Authorization become critical, as these areas govern execution safety and policy compliance at the moment of action. In environments with regulatory pressure or formal governance requirements, placing emphasis on Compliance tooling supports reporting and audit readiness.
Among the vendors shown in the landscape, NeuralTrust is the only platform that covers Posture, Runtime Protection, and Runtime Authorization, the core loop needed to both observe behavior and act on it with enforcement and policy gating. This combination matters because many agent failures are cross-layer events: a behavior anomaly may lead to a risky tool call, which in turn triggers an impact unless it is blocked or approved. A solution that connects observation, real-time execution control, and authorization reduces gaps between detection and prevention, an increasingly important distinction as agents scale across tools, teams, and environments.
If you are interested in other of our competitive landscape analysis, check our “Top 10 AI Agent Security platforms” or the “Gartner Top 8 AI Gateways”.











